CCNA With Ethical Hacking Certification Training
Discover the depths of CCNA With Ethical Hacking Technology. Join us now to gain comprehensive insights into CCNA With Ethical Hacking technology from a seasoned professional.
![]() 5.0 out of 5 based on 119 user reviews. |
5.0 out of 5 based on 119 user reviews. |  |
|  |
|  |
| 
Enquire Now
Accreditations & Affiliations
Training Features
Best Ethical Hacking Training Institute in Delhi NCR
Join Best Ethical Hacking Training in Delhi, Ethical Hacking Training Course in Delhi, Ethical Hacking Training Institute in Noida
With a huge surge in cyber crimes, companies all over the world are looking for ethical hackers who protect and fortify their corporate networks. According to a recent survey, a whopping 1.5 million cyber security experts are needed by the year 2020. Are you ready to jump on the bandwagon of ethical hacking?
An ethical or white hat tracker employs penetration tests to identify the vulnerabilities of an organisations networks and security. The penetration tests remediate vulnerabilities, reduce risk factors and tighten security.
An ethical hacker is constantly on the lookout for loopholes and strengthens the network of a company. If problem-solving is your forte and playing around with networks and security is your passion, then you’re perfectly suited to become an ethical hacker.
Get trained with the best ethical hacking training course in Noida and live your Passion!
The ethical training course from CETPA immerses students into an interactive environment where they will gain an in-depth training on how to scan, test, self-hack and make their own systems secure from intruders. CETPA offers training in an intensive lab environment so that students are not only acquainted with the theory but also gain a hands-on approach to handling the challenges of the future workplace.It is the best ethical training institute in Delhi NCR.
Students initially are taught on how real-life networks operate and they gain a first-hand experience on scanning and protecting their own networks from intruders.CETPA is the best Ethical Hacking training in Delhi NCR. They are also taught damage control and how to secure a system quickly from hackers before the issue escalates. Intrusion Detection, DDoSAttacks, Social Engineering, Virus Creation and Control, Setting a Honey Pot, Malware, Phishing, Policy Creation, and Buffer Overflows are some of the topics handled at our Ethical Hacking Course in Noida.
- Students, Graduates and Faculty
- IT professionals like Network Engineers, Web Developers, System Administrators and coders
- Law students and Professionals
- Finance & Banking Professionals
- Anyone who is interested in the mystical world of hacking
CAREER PROSPECTS
- With the increased number and sophistication of cyber attacks, espionage there is a huge demand for trained cyber security experts. Ethical hackers are the need of the hour not only for MNCs but also for government organisations.
- Banks, telecom companies, airlines, hotels, internet providers, cyber crime police departments, government agencies, e-commerce stores, and ITES companies are hiring white hat hackers to protect their systems from intruders.
- The exciting thing about working as an Ethical Hacker is the adrenaline rush and always testing your wits against unknown intruders. When you enroll in this course at CETPA, the best ethical training institute in Noida
CETPA ETHICAL TRAINING BENEFITS & HIGHLIGHTS
- Learn the Hacker Mindset and become an expert in both defensive countermeasures and offence engaging techniques
- Live Demonstration of hacking tools, techniques and methods
- Practical Hands-on approach for an in-depth understanding
- 100% Placement Assistance
- Update course material, tool kit and certification
Join CETPA for top-notch Ethical Hacking Training in Delhi, NCR or Noida Attain the Career of your Dreams. Contact us to know more.
The history of ethical hacking can be traced back to 1960 when first hackers emerged and their first victims were trains. Similarly, a group of hackers emerged around 1970 who hacked phone lines. But it was in 1974 that the U.S. Air Force conducted the first ethical hacks, which was an evaluation of Multics Operating System. The brief time-line of ethical hacking can be shown as:
- 1986 : The Computer Fraud and Abuse Act cracked down on computer crimes and ethical hacking methodologies were considered illegal without contractual agreement.
- 1995 : IBM’s john Patrick coined the term “Ethical Hacking”.
- 2003 : OWASP releases the testing guide which included penetration testing practices.
- 2009 : The penetration testing and execution standard launches common language for performing penetration test.
INDUSTRY DEMANDS AND CAREER SCOPE FOR ETHICAL HACKING
In this global world of dynamic technologies many companies like IBM, Wipro, and Infosys are employing ethical hackers as a measure to curb potential threats. According to Nasscom, India will require at least 80000 hackers as compared to 20000 hackers present in the market. Many companies are hiring for conducting Audit and suggest Fixes.
Ethical Hackers are in great demand in information security companies and ethical hacking companies. There are certain promising roles like that of Network Security Administrators, Network defense analysts, Web security Administrators, penetration Testers, etc. (to name a few..).
Usually it is observed that professionals in these industries bag 40% higher salary as compared to their counterparts. Hence choosing a career in ethical hacking is a promising bet for all the students who want to prove themselves in the IT industry.
Ethical hacking requires knowledge of the Operating System such as windows and Linux which is used as a target and host respectively. So, students should ensure to learn to work with Operating System Software.
Students must ensure that the programming languages such as HTML, C/C++, Java, PHP, Python, ruby, Lua (game Engine) must be in well command so that execution of hacking skills becomes easy. To become like a hacker one must think like a hacker.
There are certain points an ethical hacker keeps in mind while conducting the test:- How well the security system of the organization is established?
- Is there any weak point in the system which can be easily accessible to black hat hackers?
- Is there any information on the system which can be exploited by the external hackers?
- Are there any attempts by the black hat hackers to hack the organization?
CETPA Infotech Pvt. Ltd. completes 12 years of delivering training to engineering students and working professionals in the year 2015. Our focus is to provide ‘world class’ training to our students and CETPA is today one of India’s Leading training school. We have a globally accredited selection of vendor authorized training and certification programs. CETPA has several physical & satellite training centers across India and is known in Roorkee, Noida (Delhi NCR), Dehradun, and Lucknow.
CETPA offer international level Ethical Hacking training course focusing on Indian as well as foreigner students from diverse countries like: Nigeria, South Africa, USA, Bhutan and more under guidance of expert trainers. Trainee can enroll with 4/6 weeks summers training program or short term course or different training program like vocational training, regular training, etc. are offered by CETPA depending on their learning skill.
The company has expert trainers who teach about the legal methods of hacking and ensure to build confidence among the budding hackers. Moral values and Ethics are the major consideration in ethical Hacking field, so besides providing qualitative concepts, training in different levels of hacking is taken into consideration. In addition, CETPA has certain worth mentioning features
- Specialized doubt clearing classes for effective concept building.
- Theoretical concepts with live industrial projects are rigorously taught so that implementing concepts practically becomes easy.
- We deliver best training course that closely fit in day-to-day issues.
- We provide industrial training with instructors have extensive industrial experience.
- Aim to provide the best learning experience.
- Training would be delivered in Classrooms or Online: Benefit NRI students and students having distance distress.
Student’s satisfaction is our motto. We always strive to give our best. So students willing to opt their career in ethical hacking should join CETPA for fulfilling experience.
An educated individual is an asset to a society and organization. Learning is a never ending process and students must ensure to keep learning and implementing their concepts practically to mold themselves into true professionals.
COMPANIES USING ETHICAL HACKING
Top companies have very large network of systems. In order to prevent any malicious hacker to illegally utilize the information and data, almost all the companies use ethical hacking concept by employing top level hackers. Some prominent companies using this concept are
- Microsoft
- Sony
- Dell
- IBM
- Apple
All the banking organizations and all the MNCs use the concept of ethical hacking to protect their large amount of data and critical information.
Since CETPA has been for 12 years in the training market, it has developed very good contacts with the top companies of the corporate world. Therefore, it becomes quite evident that the student who has good skills developed at CETPA can surely get superb placements. In order to assist students at every level of placements a dedicated placement wing has been established to cater the needs of students. To make the students aware and have the industrial exposure along with project knowledge as well as experience, CETPA provides six months internship program to students and after the program completion placement opportunity and placement pathway is unlocked.
Please visit the link for more information on placements.Click Here
What are the benefits of doing a Ethical Hacking course?
- You will get better knowledge of programming and how to implement it for actual development requirements in the industrial projects and applications.
- Enhanced knowledge on the web development framework. Using this framework, you can develop dynamic websites swiftly.
- You will learn how to design, develop, test, support and deploy desktop, custom web, and mobile applications.
- Design and improve testing and maintenance activities and procedures.
- Design, implement and develop important applications in a Ethical Hacking environment.
- Increased chances of working in leading software companies like Infosys, Wipro, Amazon, TCS, IBM and many more.
Professional growth, increased compensation and validation of the skill are the most popular reasons why individuals and professionals seek IT certifications. Keeping this in mind, we at CETPA provide you with certification in latest and innovative technologies to help you to reach your certification goals.
CETPA is the official Training partner of Oracle, Microsoft, Autodesk, Panasonic and Nuvoton and thus provides Training as per international standards and curriculum. CETPA proudly provides you certification in association with our training partners so that you can validate your domain specific technical skills. Certification from these big brands will help you in grabbing your dream job.
IMPORTANCE OF CETPA CERTIFICATION
For individuals and IT professionals:- Gives you an advantage while searching for a job and provide a competitive advantage over your competitors.
- Ensure knowledge and skill are up to date and can be applied to the job
- Provide credibility to those looking for a career in an IT domain.
- Offer fast track to career advancement
- Demonstrate level of competency
- Professional Credibility as well as it demonstrates your dedication and motivation to professional development.
- You are likely to stand out from the crowd and be considered to be successful in your positions.
- Represent a well-recognized and valued IT credential that increases marketability and competitive edge.
- Provide peace of mind with the confidence that certified employees have truly learned the skills necessary to do their jobs;
- Express valuable credentials to search for in prospective employees, and can help retain top performers when offered as an incentive;
- Offer a competitive advantage when the team is trained and certified regularly.
Talk To Advisor
MODE/SCHEDULE OF TRAINING:
| Delivery Mode | Location | Course Duration | Schedule (New Batch Starting) |
|---|---|---|---|
| Classroom Training (Regular/ Weekend Batch) | *Noida/ *Roorkee/ *Dehradun | 4/6/12/24 Weeks | New Batch Wednesday/ Saturday |
| *Instructor-Led Online Training | Online | 40/60 Hours | Every Saturday or as per the need |
| *Virtual Online Training | Online | 40/60 Hours | 24x7 Anytime |
| College Campus Training | India or Abroad | 40/60 Hours | As per Client’s need |
| Corporate Training (Fly-a-Trainer) | Training in India or Abroad | As per need | Customized Course Schedule |
Course Content
- Information Security Overview
- Information Security Threats and Attack Vectors
- Top Information Security Attack Vectors
- Motives, Goals, and Objectives of Information Security Attacks
- Information Security Threats
- Information Warfare
- IPv6 Security Threats
- Hacking Concepts
- Hacking vs. Ethical Hacking
- Effects of Hacking on Business
- Who Is a Hacker?
- Hacker Classes
- Hacktivism
- Hacking Phases
- Types of Attacks
- Types of Attacks on a System
- Operating System Attacks
- Misconfiguration Attacks
- Application-Level Attacks
- Skills of an Ethical Hacker
- Defense in Depth
- Incident Management Process
- Information Security Policies
- Classification of Security Policies
- Structure and Contents of Security Policies
- Footprinting Concepts
- Footprinting Terminology
- What is Footprinting?
- Why Footprinting?
- Objectives of Footprinting
- Footprinting Threats
- Footprinting through Search Engines
- Finding Company’s External and Internal URLs
- Mirroring Entire Website
- Website Mirroring Tools
- Extract Website Information from http://www.archive.org
- Monitoring Web Updates Using Website Watcher
- Finding Resources Using Google Advance Operator
- Google Hacking Tool: Google Hacking Database (GHDB)
- Google Hacking Tools
- WHOIS Footprinting
- WHOIS Lookup
- DNS Footprinting
- Extracting DNS Information
- DNS Interrogation Tools
- Network Footprinting
- Locate the Network Range
- Determine the Operating System
- Footprinting through Social Engineering
SCANNING NETWORKS
- Check for Live Systems
- Checking for Live Systems - ICMP Scanning
- Ping Sweep
- Check for Open Ports
- Scanning Tool: Nmap
- Hping2 / Hping3
- Scanning Techniques
- Scanning Tool: NetScan Tools Pro
- Scanning Tools
- Do Not Scan These IP Addresses (Unless you want to get into trouble)
- Port Scanning Countermeasures
- Banner Grabbing Countermeasures: Disabling or Changing Banner
- Hiding File Extensions from Web Pages
- Scan for Vulnerability
- Proxy Servers
- Why Attackers Use Proxy Servers?
- Use of Proxies for Attack
ENUMERATION
- What is Enumeration?
- Techniques for Enumeration
- Services and Ports to Enumerate
- NetBIOS Enumeration
- NetBIOS Enumeration
- NetBIOS Enumeration Tool: SuperScan
- NetBIOS Enumeration Tool: Hyena
- NetBIOS Enumeration Tool: Winfingerprint
- NetBIOS Enumeration Tool: NetBIOS Enumerator
- Enumerating User Accounts
- Information at Hand Before System Hacking Stage
- System Hacking: Goals
- CEH Hacking Methodology (CHM)
- CEH System Hacking Steps
- CrackingPasswords
- Password Cracking
- Password Complexity
- Password Cracking Techniques
- Types of Password Attacks
- Distributed Network Attack
- Default Passwords
- Manual Password Cracking (Guessing)
- Stealing Passwords Using Keyloggers
- Spyware
- How to Defend Against Keyloggers
- Anti-Spywares
- What Is Steganography?
- Least Significant Bit Insertion
TROJANS AND BACKDOORS
- Trojan Concepts
- What is a Trojan?
- Trojan Infection
- Types of Trojans
- Command Shell Trojans
- Command Shell Trojan: Netcat
- GUI Trojan: MoSucker
- GUI Trojan: Jumper and Biodox
- Document Trojans
- E-mail Trojans
- E-mail Trojans: RemoteByMail
- Trojan Detection
- How to Detect Trojans
- Scanning for Suspicious Ports
- Trojan Horse Construction Kit
- Anti-Trojan Software
VIRUSES AND WORMS
- Virus and Worms Concepts
- Introduction to Viruses
- Virus and Worm Statistics
- Types of Viruses
- System or Boot Sector Viruses
- File and Multipartite Viruses
- Macro Viruses
- Cluster Viruses
- Stealth/Tunneling Viruses
- Encryption Viruses
- Polymorphic Code
- Computer Worms
- Malware Analysis
- Online Malware Testing: VirusTotal
- Online Malware Analysis Services
- Anti-virus Tools
SNIFFERS
- Sniffing Concepts
- Wiretapping
- Lawful Interception
- Packet Sniffing
- Sniffing Threats
- SPAN Port
- MAC Attacks
- MAC Flooding
- MAC Address/CAM Table
- How CAM Works
- DHCP Attacks
- How DHCP Works
- DHCP Request/Reply Messages
- IPv4 DHCP Packet Format
- ARP Poisoning
- What Is Address Resolution Protocol (ARP)?
- ARP Spoofing Techniques
- ARP Spoofing Attack
- Spoofing Attack
- Spoofing Attack Threats
- DNS Poisoning
- DNS Poisoning Techniques
- Social Engineering Concepts
- What is Social Engineering?
- Behaviors Vulnerable to Attacks
- Social Engineering Techniques
- Types of Social Engineering
- Human-based Social Engineering
- Technical Support Example
- Authority Support Example
- Social Networking Sites
- Social Engineering Through Impersonation on Social Networking Sites
- How to Detect Phishing Emails
- Anti-Phishing Toolbar: Netcraft
- Anti-Phishing Toolbar: PhishTank
- Identity Theft Countermeasures
1. INTRODUCTION TO ETHICAL HACKING
- Information Security Overview
- Information Security Threats and Attack Vectors
- Top Information Security Attack Vectors
- Motives, Goals, and Objectives of Information Security Attacks
- Information Security Threats
- Information Warfare
- IPv6 Security Threats
- Hacking Concepts
- Hacking vs. Ethical Hacking
- Effects of Hacking on Business
- Who Is a Hacker?
- Hacker Classes
- Hacktivism
- Hacking Phases
- Types of Attacks
- Types of Attacks on a System
- Operating System Attacks
- Misconfiguration Attacks
- Application-Level Attacks
- Skills of an Ethical Hacker
- Defense in Depth
- Incident Management Process
- Information Security Policies
- Classification of Security Policies
- Structure and Contents of Security Policies
SOCIAL ENGINEERING
- ng Threats
- Footprinting through Search Engines
- Finding Company’s External and Internal URLs
- Mirroring Entire Website
- Website Mirroring Tools
- Extract Website Information from http://www.archive.org
- Monitoring Web Updates Using Website Watcher
- Finding Resources Using Google Advance Operator
- Google Hacking Tool: Google Hacking Database (GHDB)
- Google Hacking Tools
- WHOIS Footprinting
- WHOIS Lookup
- DNS Footprinting
- Extracting DNS Information
- DNS Interrogation Tools
- Network Footprinting
- Locate the Network Range
- Determine the Operating System
- Footprinting through Social Engineering
- DoS/DDoS Concepts
- What is a Denial of Service Attack?
- What Are Distributed Denial of Service Attacks?
- Symptoms of a DoS Attack
- DoS Attack Techniques
- Bandwidth Attacks
- Service Request Floods
- SYN Attack
- SYN Flooding
- ICMP Flood Attack
- Peer-to-Peer Attacks
- Permanent Denial-of-Service Attack
- Application Level Flood Attacks
- Botnet
- Botnet Propagation Technique
- DDoS Attack
- DDoS Attack Tool: LOIC
- DoS Attack Tools
SESSION HIJACKING
- Session Hijacking Concepts
- What is Session Hijacking?
- Dangers Posed by Hijacking
- Why Session Hijacking is Successful?
- Key Session Hijacking Techniques
- Brute Forcing Attack
- Network-level Session Hijacking
- The 3-Way Handshake
- Sequence Numbers
- Session Hijacking Tools
- Session Hijacking Tool: Zaproxy
- Session Hijacking Tool: Burp Suite
- Session Hijacking Tool: JHijack
- Session Hijacking Tools
HACKING WEBSERVERS
- Webserver Concepts
- Webserver Market Shares
- Open Source Webserver Architecture
- Attack Methodology
- Webserver Attack Methodology
- Webserver Attack Methodology: Information Gathering
- Webserver Attack Methodology: Webserver Footprinting
- Counter-measures
- Countermeasures: Patches and Updates
- Countermeasures: Protocols
- Countermeasures: Accounts
- Countermeasures: Files and Directories
- How to Defend Against Web Server Attacks
- How to Defend against HTTP Response Splitting and Web Cache Poisoning
- Web Server Penetration Testing
HACKING WEB APPLICATIONS
- Web App Concepts
- Web Application Security Statistics
- Introduction to Web Applications
- SQL Injection Attacks
- Command Injection Attacks
- Web App Hacking Methodology
- Footprint Web Infrastructure
- Footprint Web Infrastructure: Server Discovery
- Hacking Web Servers
- Web Server Hacking Tool: WebInspect
- Web Services Probing Attacks
- Web Service Attacks: SOAP Injection
- Web Service Attacks: XML Injection
- Web Services Parsing Attacks
- Web Service Attack Tool: soapUI
SQL INJECTION
- SQL Injection Concepts
- SQL Injection
- Scenario
- SQL Injection Threats
- What is SQL Injection?
- SQL Injection Attacks
- SQL Injection Detection
- Types of SQL Injection
- Simple SQL Injection Attack
- Union SQL Injection Example
- SQL Injection Error Based
- Blind SQL Injection
- What is Blind SQL Injection?
- SQL Injection Methodology
- Advanced SQL Injection
- Information Gathering
- Extracting Information through Error Messages
- Interacting with the FileSystem
- SQL Injection Tools
- SQL Injection Tools: BSQLHacker
- SQL Injection Tools: Marathon Tool
- SQL Injection Tools: SQL Power Injector
- SQL Injection Tools: Havij
- SQL Injection Tools
- Wireless Concepts
- Wireless Networks
- Wi-Fi Networks at Home and Public Places
- Types of Wireless Networks
- Wireless Encryption
- Wireless Threats
- Wireless Threats: Access Control Attacks
- Wireless Threats: Integrity Attacks
- Footprint the Wireless Network
- Attackers Scanning for Wi-Fi Networks
- Bluetooth Hacking
- Bluetooth Threats
EVADING IDS, FIREWALLS, AND HONEYPOTS
- IDS, Firewall and Honeypot Concepts
- How IDS Works?
- Ways to Detect an Intrusion
- Denial-of-Service Attack (DoS)
- ASCII Shellcode
- Other Types of Evasion
- Evading Firewalls
- IP Address Spoofing
- Source Routing
- Website Surfing Sites
- Detecting Honeypots
- Detecting Honeypots
BUFFER OVERFLOW
- Buffer Overflow Concepts
- Buffer Overflow
- Shellcode
- No Operations (NOPs)
- Buffer Overflow Methodology
- Overflow using Format String
- Smashing the Stack
- Once the Stack is Smashed...
- Buffer Overflow Security Tools
- BoF Security Tool: BufferShield
- BoF Security Tools
CRYPTOGRAPHY
- Cryptography Concepts
- Cryptography
- Types of Cryptography
- Government Access to Keys (GAK)
- Encryption Algorithms
- Ciphers
- Advanced Encryption Standard (AES)
- Public Key Infrastructure(PKI)
- Public Key Infrastructure (PKI)
- Certification Authorities
- Email Encryption
- Digital Signature
- SSL (Secure Sockets Layer)
- Transport Layer Security (TLS)
- Disk Encryption Tools
- Cryptanalysis Tool: CrypTool
- Cryptanalysis Tools
- Online MD5 Decryption Tool
PENETRATION TESTING
- Pen Testing Concepts
- Security Assessments
- Security Audit
- Vulnerability Assessment
- Limitations of Vulnerability Assessment
- Introduction to Penetration Testing
- Penetration Testing
- Why Penetration Testing?
- Testing Locations
- Types of Pen Testing
- Types of Penetration Testing
- External Penetration Testing
- Internal Security Assessment
- Black-box Penetration Testing
- Grey-box Penetration Testing
- White-box Penetration Testing
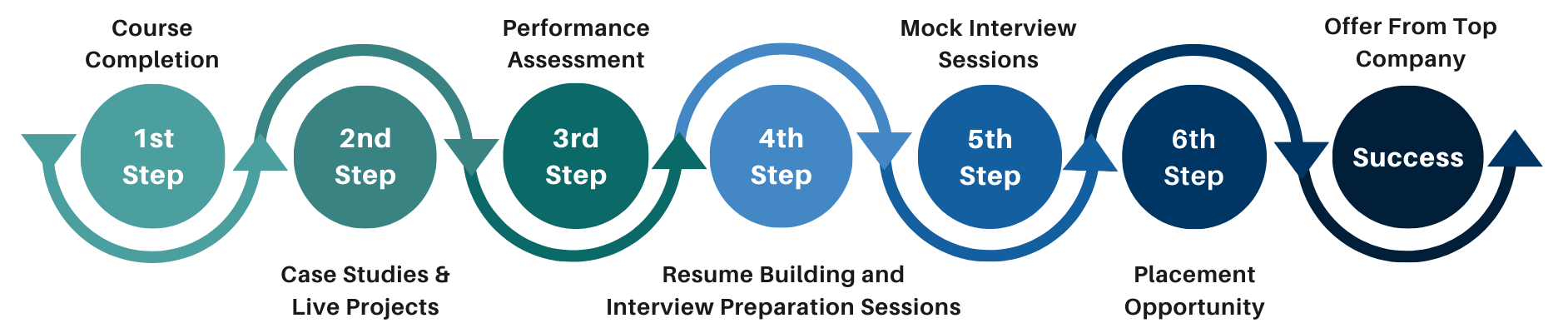
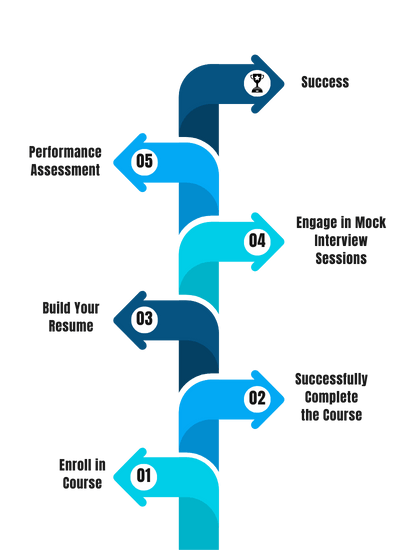
Our Process
FAQ'S
- Classroom Training
- Online Training
- Corporate Training
- On campus Training
Career Assistance
- Build an Impressive Resume
- Attend Mock-Up Interviews with Experts
- Get Interviews & Get Hired
Training Certification
Earn your certificate
Your certificate and skills are vital to the extent of jump-starting your career and giving you a chance to compete in a global space.
Share your achievement
Talk about it on Linkedin, Twitter, Facebook, boost your resume or frame it- tell your friend and colleagues about it.
Upcoming Batches
What People Say
Our Partners
Need Customized Curriculum? Request Now
Structure your learning and get a certificate to prove it.

Our Clients

Our Placed Students
Related Courses
Review Us
Nikhil Shishodia
![]() Tuesday, 18 April 2017
Tuesday, 18 April 2017
4 Weeks Ethical Hacking Training In Lucknow
CETPA Provide Smart Labs with Real Latest Equipment. 24x7 Lab Facilities. Students are free to access the labs for unlimited number of hours as per their own preferred timings.
Neha Kaushik
![]() Monday, 10 April 2017
Monday, 10 April 2017
Ethical Hacking Training In Noida
I had a wonderful experience with cetpa. it's a best place for doing training in any technology I have also completed my training in ethical hacking from cetpa . The best thing of the training was the practical part they mostly concentrate on practical session which is must to learn the any technology now I am very good in ethical hacking and also got the job in a very good company. Cetpa also provides the placement facility to their students. I am really thankful to all the members of cetpa.
S.Kumar
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Training Center In Noida
This is The Advance Hacking Techniques Program Provide by CETPA INFOTECH in Noida . We learn to be safe from CETPA IFOTECH who breaks the computer security, network security, Network mobile Security, web application security, cyber forensics etc.
Rahul
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Course In Noida
We learn to be safe from CETPA IFOTECH who breaks the computer security, network security, Network mobile Security, web application security, cyber forensics etc.
TRIpathi
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Course
Our Training impart hacking skills as well defensive techniques as the cyber world organisations need to be safe. All such must be aware of hacking techniques to ensure cyber Security. Our approach is more practical in comparison to theory. i like to thank CETPA INFOTECH help me to growth my career.
TRAPTHI
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Training In Noida
Our Training impart hacking skills as well defensive techniques as the cyber world organisations need to be safe. All such must be aware of hacking techniques to ensure cyber Security. Our approach is more practical in comparison to theory. i like to thank CETPA INFOTECH help me to growth my career.
POOJA GARG
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Training
I am POOJA GARG , I COMPLETED MY B.Tech from Information Technology. Now I am working in software company as a DATA SECURITY ANALYST. I have done ETHICAL HACKING AND CYBER SECURITY training at CETPA.
PAYAL SINGH
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Training Classes
The training was very useful to get this job easily. CETPA have advanced technologies with updated syllabus. I feel the training is really worth for my money, Also cetpa provide me placement oriented training. They provide placements also.
MANISH SINGH
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Training Institute In Noida
The CETPA is very good TRAINING ORGANIZATION, I would suggest before you embark on that level of certification, you gain a solid understanding of Linux, Ethical Hacking,networking.
MAHI RAJ
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Ethical Hacking Institute In Noida
I would also suggest the ETHICAL Hacking from CETPA , is a much more rounded course and provides an excellent standard. The CETPA instructors are amazingly passionate about security and are all experienced in their fields.
ABHAY SINGH
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Best Ethical Hacking Training In Noida
The CETPA instructors are amazingly passionate about security and are all experienced in their fields.
BANTY PAL
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
6 Months Hacking Training
I would also suggest the ETHICAL Hacking from CETPA , CETPA instructors are amazingly passionate about security and are all experienced in their fields.
RAVI KUMAR
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
6 Weeks Hacking Training
If you are looking into anything security related, or even plan to be an admin I would think it beneficial. CETPA INFOTECH IS ONE OF LEADING INDUSTRY AND IT COMPANY IN INDIA, PROVIDE CYBER SECURITY TRAINIG -i learn about possible attack vectors -i turn you learn how to harden those vectors for better security -i you will be able to better identify WHEN these things happen
Shalini Pathania
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Hacking Training In Noida
cetpa provided me a very advanced concept about Ethical Hacking & Cyber Forensic
Jhalki Bharadwaj
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
Hacking Training Institute
i completed my 6 month training of cyber security from cetpa , noida
Kritika
![]() Saturday, 15 April 2017
Saturday, 15 April 2017
6 Weeks Hacking Training In Noida
Advance Hacking Techniques Program Provide by CETPA , Noida. system hacking concept is on the advanced training for my career
Ayush Kumar
![]() Tuesday, 18 April 2017
Tuesday, 18 April 2017
Ethical Hacking Training
CETPA is the leader in offering placement to the students, as it has a dedicated placement wing which caters to the needs of the students during placements.
Amit Bhandari
![]() Tuesday, 18 April 2017
Tuesday, 18 April 2017
4 Weeks Ethical Hacking Training
CETPA conducts Personality Development sessions including Spoken English, Group Discussions, Mock Interviews, Presentation skills to prepare students to face challenging interview situation with ease.
Sachin Kuttapan
![]() Tuesday, 18 April 2017
Tuesday, 18 April 2017
4 Weeks Ethical Hacking Training In Noida
Mentors of ethical hacking training in CETPA Noida helps in major project training, minor project training, live project preparation, interview preparation and job placement support.
Course Features
- Lectures 0
- Quizzes 0
- Duration 10 weeks
- Skill level All levels
- Language English
- Students 0
- Assessments Yes