CCNP Security Certification Training
Discover the depths of CCNP Security Technology. Join us now to gain comprehensive insights into CCNP Security technology from a seasoned professional.
![]() 5 out of 5 based on 101 user reviews. |
5 out of 5 based on 101 user reviews. |  |
|  |
|  |
| 
Enquire Now
Accreditations & Affiliations
Training Features
Best CCNP Security Training Institute in Delhi NCR
Join Best CCNP Security Online Training in Delhi, CCNP Security Online Training Course in Delhi, CCNP Security Online Training Institute in Noida
The (CCNP Security) CISCO Certified Network Professional Security certification program offered at CETPA is designed in a way to exactly match the job responsibilities of a CISCO Network Security Engineer who is responsible for the Security of Switches, Routers, appliances, and Networking devices. The training also provides theoretical and practical knowledge about selecting, deploying, troubleshooting and supporting IDS/IPS, firewalls, and VPS solutions for the networking requirements.
Our CCNP training class in Noida is ideal for Network Security Engineers who want to accelerate their career which now requires them to have a holistic end-to-end understanding of the entire security infrastructure. The course is an efficient way for the engineers to ensure that they have all the required skills and knowledge required for servicing, maintaining, and supporting CISCO network security solutions. CCNP Security provides technical know-how of enforcing cyber security performance, meet compliance standards, and get high-quality security service levels.
CCNP Certification was established by CISCO in the year 1998 along with CCNA Certification. As this was the first professional-level certification by CISCO, it has anexcellent reputation of being a certificate which confirms high network security knowledge.
The certification lays a major emphasis on routing and switching along with a number of other topics. Currently, CCNP Security Certification requires an individual to only clear three exams as compared to fours exams in the past. The current version of the certificate majorly focuses on ROUTE and SWITCH skills.
With more than 13 years of experience in the industry, our CCNP training class in Noida is one of the most popular. Right from our curriculum, faculty, to our world-class IT labs, everything in line to our ideology of providing our students a rich combination of theoretical and practical knowledge in an environment which helps them grow as a professional.
Apart from full-time courses, we also offer vocational CCNP security training as well as short-term courses to help engineers learn the latest network security technologies and boost their career as a network security engineer. Moreover, we also offer online courses Indian as well as students from other countries.
Some the reasons that make us the best CCNP training institute in Noida are
- Carefully designed curriculum to help students clear CCNP Security exam
- Qualified and experienced faculty
- Flexible batch timings
- World-class IT labs
- Online courses
- Notes and books provided by the company
- Workshops to help students get exposed to live projects
We also offer placement assistance to our students and have a special placement wing at our companY for the same. We have placed hundreds of our CCNP certified professionals in a number of reputable IT companies throughout the country. Many of your students now hold senior positions in the companies which again are a sign of the high-quality training provided by our CCNP training institute in Noida.
Get in touch with us today or chat online through our official website to know more about the CCNP Security course offered at CETPA!
CCNP has its roots back as to 1998, when Cisco announced both CCNA and CCNP. As Cisco’s first Professional-level certification, CCNP has a solid reputation as a cert that implies a high level of skill.
CCNP has always had a heavy focus on routing and switching, with a variety of other topics. At times, the focus was on WAN topics and troubleshooting. In the CCNP from 2006-2010, troubleshooting was gone as an exam, but the exams covered security, QoS, and IP multicast. Today’s CCNP certification requires just 3 exams, rather than the 4 exams in comparison to older CCNP certs. This version of CCNP focuses almost entirely on ROUTE and SWITCH skills. TSHOOT focuses on troubleshooting, with the majority of topics coming from the ROUTE and SWITCH topics.
CCNP Security certification offers employers a substantial proof of experienced and professionally equipped network security engineers with job-ready training and skills for today’s demanding security environment. According to the Industry estimates, the expert forecast shows that in the next five years, the industry will need twice the number of network security professionals, and most of them will be recognized by a quality industry certifications. Further the CCNP certification offers tangible results that are mentioned as under
- The Certification adopts the best practice for Network Security Engineering.
- It fulfills the demand for Network Security Practical Skills.
CCNP security is a professional level certification in managing Security Infrastructure and work efficiently in handling routers, switches and all the networking devices. But before going for the CCNP certifications candidates needs to
- Prove his/her efficiency in the CCNA, CCNA Security and CCNP.
- In addition a valid CCNA Security Certification or any CCIE Certification can act as a prerequisite.
- Learning will become easier after going through different associate level certifications.
- Further the student should prepare his/her mind to get the CCNP Security certification in minimum possible time.
CETPA is a growing IT Training and Services Provider determined to set high standards in IT industry. CETPA is a training school offering CCNP Security training with choice of multiple training locations across India like: , Noida (Delhi-NCR), Roorkee, Dehradun and Lucknow.
CCNP Security training is a job-ready program for the Cisco Network Security Engineer responsible for security in routers, switches, networking devices, and appliances. This certification validates skills in choosing, deploying, supporting, and troubleshooting Firewalls, VPNS, and IDS/IPS solutions for their networking environments. CETPA is recognized as the best CCNP Security training company of India because of specific features that differentiate them with others. Few are
- Specialized in localized classes to enable students attend the lectures through an interactive session.
- CETPA provides Online CCNP Security training classes to assist the NRI students with virtual learning of technology.
- CETPA brings the latest certifications that are in demand in the industry.
- Prepare trainee for academic as well as professional success.
- Qualified and professional instructors provide CCNP Security training.
- Workshop to aid trainee get exposed to real-life projects.
Vocational CCNP Security training and short term course provided by CETPA equips network security engineers with in-depth knowledge and practical skills required to secure the network environment using existing Cisco IOS Software router- and switch-based networks, and provide security services based on install and configure components of the Cisco IOS Software.
CETPA has provided 4/6 weeks CCNP Security training for students to advance their network security skill and expertise them with the technology at international level. This will benefit them with learning that will avail them with job opportunity in Indian as well as abroad based company immediately after CCNP Security training completion. Some of the top companies where CCNP Security certified professionals can find top notch jobs are
- Cisco
- Dell
- Orange Networking
All the IT and Networking companies hire CCNP security certified professionals to meet their security infrastructure needs. Good pay packages and good designations in reputed MNCs are prominently offered to deserving candidates.
Industrial Training is the important strategy to expose engineering students to real work life situations and to equip them with the necessary skills that intensify their job acumen. CCNP Security certification program offered by CETPA is aligned particularly to the job role of the Cisco Network Security Engineer responsible for Security in Networking devices, appliances, Routers and Switches, as well as choosing, supporting, deploying and troubleshooting Firewalls, IDS/IPS, and VPNs solutions for their networking environments.
Our quality of education speaks for itself when our students are placed in reputed organizations and excel in their field. CETPA have a proven track record of placement for years together. Our main strength is our own past students working in various technologies in different companies. Our past students, holding higher level positions, represent the effective training provided by our company.
We have established excellent rapport with well reputed companies. Many companies have been tied up with our company for training, placement, exchange of faculty and guest lectures. For a comprehensive list of placements offered to students, please visit the link given Click Here.
- You will get better knowledge of programming and how to implement it for actual development requirements in the industrial projects and applications.
- Enhanced knowledge on the web development framework. Using this framework, you can develop dynamic websites swiftly.
- You will learn how to design, develop, test, support and deploy desktop, custom web, and mobile applications.
- Design and improve testing and maintenance activities and procedures.
- Design, implement and develop important applications in a CCNP Security environment.
- Increased chances of working in leading software companies like Infosys, Wipro, Amazon, TCS, IBM and many more.
Professional growth, increased compensation and validation of the skill are the most popular reasons why individuals and professionals seek IT certifications. Keeping this in mind, we at CETPA provide you with certification in latest and innovative technologies to help you to reach your certification goals.
CETPA is the official Training partner of Oracle, Microsoft, Autodesk, Panasonic and Nuvoton and thus provides Training as per international standards and curriculum. CETPA proudly provides you certification in association with our training partners so that you can validate your domain specific technical skills. Certification from these big brands will help you in grabbing your dream job.
IMPORTANCE OF CETPA CERTIFICATION
For individuals and IT professionals:- Gives you an advantage while searching for a job and provide a competitive advantage over your competitors.
- Ensure knowledge and skill are up to date and can be applied to the job
- Provide credibility to those looking for a career in an IT domain.
- Offer fast track to career advancement
- Demonstrate level of competency
- Professional Credibility as well as it demonstrates your dedication and motivation to professional development.
- You are likely to stand out from the crowd and be considered to be successful in your positions.
- Represent a well-recognized and valued IT credential that increases marketability and competitive edge.
- Provide peace of mind with the confidence that certified employees have truly learned the skills necessary to do their jobs;
- Express valuable credentials to search for in prospective employees, and can help retain top performers when offered as an incentive;
- Offer a competitive advantage when the team is trained and certified regularly.
Talk To Advisor
MODE/SCHEDULE OF TRAINING:
| Delivery Mode | Location | Course Duration | Schedule (New Batch Starting) |
|---|---|---|---|
| Classroom Training (Regular/ Weekend Batch) | *Noida/ *Roorkee/ *Dehradun | 4/6/12/24 Weeks | New Batch Wednesday/ Saturday |
| *Instructor-Led Online Training | Online | 40/60 Hours | Every Saturday or as per the need |
| *Virtual Online Training | Online | 40/60 Hours | 24x7 Anytime |
| College Campus Training | India or Abroad | 40/60 Hours | As per Client’s need |
| Corporate Training (Fly-a-Trainer) | Training in India or Abroad | As per need | Customized Course Schedule |
Course Content
- Threat Defense
- Implement firewall (ASA or IOS depending on which supports the implementation)
- Implement ACLs
- Implement static/dynamic NAT/PAT
- Implement object groups
- Describe threat detection features
- Implement botnet traffic filtering
- Configure application filtering and protocol inspection
- Describe ASA security contexts
- Implement Layer 2 Security
- Configure DHCP snooping
- Describe dynamic ARP inspection
- Describe storm control
- Configure port security
- Describe common Layer 2 threats and attacks and mitigation
- Describe MACSec
- Configure IP source verification
- Configure device hardening per best practices
- Routers
- Switches
- Firewalls
- Implement SSHv2, HTTPS, and SNMPv3 access on the network devices
- Implement RBAC on the ASA/IOS using CLI and ASDM
- Describe Cisco Prime Infrastructure
- Functions and use cases of Cisco Prime
- Device Management
- Describe Cisco Security Manager (CSM)
- Functions and use cases of CSM
- Device Management
- Implement Device Managers
- Implement ASA firewall features using ASDM
- Configure NetFlow exporter on Cisco Routers, Switches, and ASA
- Implement SNMPv3
- Create views, groups, users, authentication, and encryption
- Implement logging on Cisco Routers, Switches, and ASA using Cisco best practices
- Implement NTP with authentication on Cisco Routers, Switches, and ASA
- Describe CDP, DNS, SCP, SFTP, and DHCP
- Describe security implications of using CDP on routers and switches
- Need for dnssec
- Monitor firewall using analysis of packet tracer, packet capture, and syslog
- Analyze packet tracer on the firewall using CLI/ASDM
- Configure and analyze packet capture using CLI/ASDM
- Analyze syslog events generated from ASA
THREAT DEFENSE ARCHITECTURES
- Design a Firewall Solution
- High-availability
- Basic concepts of security zoning
- Transparent & Routed Modes
- Security Contexts
- Layer 2 Security Solutions
- Implement defenses against MAC, ARP, VLAN hopping, STP, and DHCP rogue attacks
- Describe best practices for implementation
- Describe how PVLANs can be used to segregate network traffic at Layer 2
SECURITY COMPONENTS AND CONSIDERATIONS
- Describe security operations management architectures
- Single device manager vs. multi-device manager
- Describe Data Center security components and considerations
- Virtualization and Cloud security
- Describe Collaboration security components and considerations
- Basic ASA UC Inspection features
- Describe common IPv6 security considerations
- Unified IPv6/IPv4 ACL on the ASA
- Content Security
- Cisco ASA 5500-X NGFW Security Services
- Describe features and functionality
- Implement web usage control (URL-filtering, reputation based, file filtering)
- Implement AVC
- Implement decryption policies
- Describe traffic redirection and capture methods
- Cisco Cloud Web Security
- Describe features and functionality
- Implement IOS and ASA connectors
- Implement AnyConnect web security module
- Describe web usage control
- Implement AVC
- Implement anti-malware
- Describe decryption policies
- Cisco WSA
- Describe features and functionality
- Implement data security
- Implement WSA Identity and Authentication, including Transparent User Identification
- Describe web usage control
- Implement AVC
- Implement anti-malware
- Describe decryption policies
- Describe traffic redirection and capture methods (Explicit Proxy vs. Transparent Proxy)
- Cisco ESA
- Describe features and functionality
- Implement email encryption
- Implement anti-spam policies
- Implement virus outbreak filter
- Implement DLP policies
- Implement anti-malware
- Implement inbound and outbound mail policies and authentication
- Describe traffic redirection and capture methods
- Cisco ASA 5500-X NGFW Security Services
THREAT DEFENSE
- Network IPS
- Implement traffic redirection and capture methods
- Implement network IPS deployment modes
- Describe signatures engines
- Implement event actions & overrides/filters
- Implement anomaly detection
- Implement risk ratings
- Describe IOS IPS
- Configure device hardening per best practices
- IPS
- Content Security appliances
DEVICE GUIS AND SECURED CLI
- Content Security
- Implement HTTPS and SSH access
- Describe configuration elements
- Implement ESA GUI for message tracking
TROUBLESHOOTING, MONITORING, AND REPORTING TOOLS
- Configure IME and IP logging for IPS
- Content Security
- Describe reporting functionality
- Implement the WSA Policy Trace tool
- Implement the ESA Message Tracking tool
- Implement the ESA Trace tool
- Use web interface to verify traffic is being redirected to CWS
- Use CLI on IOS to verify CWS operations
- Use CLI on ASA to verify CWS operations
- Use the PRSM Event Viewer to verify ASA NGFW operations
- Describe the PRSM Dashboards and Reports
- Monitor Cisco Security IntelliShield
- Describe at a high level the features of the Cisco Security IntelliShield Alert Manager Service
THREAT DEFENSE ARCHITECTURES
- Design IPS solution
- Deploy Inline or Promiscuous
- Deploy as IPS appliance, IPS software or hardware module or IOS IPS
- Describe methods of IPS appliance load-balancing
- Describe the need for Traffic Symmetry
- Inline modes comparison – inline interface pair, inline VLAN pair, and inline VLAN group
- Management options
CONTENT SECURITY ARCHITECTURES
- Design Web Security solution
- Compare ASA NGFW vs. WSA vs. CWS
- Compare Physical WSA vs. Virtual WSA
- List available CWS connectors
- Design Email Security solution
- Compare Physical ESA vs. Virtual ESA
- Describe Hybrid mod
- Design Application Security solution
- Describe the need for application visibility and control
- Identity Management and Secure Access
- Implement device administration
- Compare and select AAA options
- TACACS+
- RADIUS
- Describe Native AD and LDAP
- Describe identity management
- Describe features and functionality of authentication and authorization
- Describe identity store options (i.e., LDAP, AD, PKI, OTP, Smart Card, local)
- Implement accounting
- Implement wired/wireless 802.1X
- Describe RADIUS flows
- AV pairs
- EAP types
- Describe supplicant, authenticator, and server
- Supplicant options
- 802.1X phasing (monitor mode, low impact, closed mode)
- AAA server
- Network access devices
- Implement MAB
- Describe the MAB process within an 802.1X framework
- Flexible authentication configuration
- ISE authentication/authorization policies
- ISE endpoint identity configuration
- Verify MAB Operation
- Implement network authorization enforcement
- dACL
- Dynamic VLAN assignment
- Describe SGA
- Named ACL
- CoA
- Implement Central Web Authentication (CWA)
- Describe the function of CoA to support web authentication
- Configure authentication policy to facilitate CWA
- URL redirect policy
- Redirect ACL
- Customize web portal
- Verify central web authentication operation
- Implement profiling
- Enable the profiling services
- Network probes
- IOS Device Sensor
- Feed service
- Profiling policy rules
- Utilize profile assignment in authorization policies
- Verify profiling operation
- Implement guest services
- Managing sponsor accounts
- Sponsor portals
- Guest portals
- Guest Policies
- Self registration
- Guest activation
- Differentiated secure access
- Verify guest services operation
- Implement posture services
- Describe the function of CoA to support posture services
- Agent options
- Client provisioning policy and redirect ACL
- Posture policy
- Quarantine/remediation
- Verify posture service operation
- Implement BYOD access
- Describe elements of a BYOD policy
- Device registration
- My devices portal
- Describe supplicant provisioning
- Implement device administration
- Describe TrustSec Architecture
- SGT Classification – dynamic/static
- SGT Transport – inline tagging and SXP
- SGT Enforcement – SGACL and SGFW
- MACsec
TROUBLESHOOTING, MONITORING, AND REPORTING TOOLS
- Troubleshoot identity management solutions
- Identify issues using authentication event details in Cisco ISE
- Troubleshoot using Cisco ISE diagnostic tools
- Troubleshoot endpoint issues
- Use debug commands to troubleshoot RADIUS and 802.1X on IOS switches and wireless controllers
- Troubleshoot backup operations
THREAT DEFENSE ARCHITECTURES
- Design highly secure wireless solution with ISE
- Identity Management
- 802.1X
- MAB
- Network authorization enforcement
- CWA
- Profiling
- Guest Services
- Posture Services
- BYOD Access
DESIGN IDENTITY MANAGEMENT ARCHITECTURES
- Device administration
- Identity Management
- Profiling
- Guest Services
- Posturing Services
- BYOD Access
SECURE MOBILITY SOLUTIONS
- Secure Communications
- Site-to-site VPNs on routers and firewalls
- Describe GETVPN
- Implement IPsec (with IKEv1 and IKEv2 for both IPV4 & IPV6)
- Implement DMVPN (hub-Spoke and spoke-spoke on both IPV4 & IPV6)
- Implement FlexVPN (hub-Spoke on both IPV4 & IPV6) using local AAA
- Implement remote access VPNs
- Implement AnyConnect IKEv2 VPNs on ASA and routers
- Implement AnyConnect SSLVPN on ASA and routers
- Implement clientless SSLVPN on ASA and routers
- Implement FLEX VPN on routers
- Site-to-site VPNs on routers and firewalls
TROUBLESHOOTING, MONITORING, AND REPORTING TOOLS (AS IMPLEMENTED ABOVE)
- Troubleshoot VPN using ASDM & CLI
- Troubleshoot IPsec
- Troubleshoot DMVPN
- Troubleshoot FlexVPN
- Troubleshoot AnyConnect IKEv2 and SSL VPNs on ASA and routers
- Troubleshoot clientless SSLVPN on ASA and routers
- Design site-to-site VPN solutions
- Identify functional components of GETVPN, FlexVPN, DMVPN, and IPsec
- VPN technology considerations based on functional requirements
- High availability considerations
- Identify VPN technology based on configuration output
- Design remote access VPN solutions
- Identify functional components of FlexVPN, IPsec, and Clientless SSL
- VPN technology considerations based on functional requirements
- High availability considerations
- Identify VPN technology based on configuration output
- Identify AnyConnect client requirements
- Clientless SSL browser and client considerations/requirements
- Identify split tunneling requirements
- Describe encryption, hashing, and Next Generation Encryption (NGE)
- Compare and contrast Symmetric and asymmetric key algorithms
- Identify and describe the cryptographic process in VPNs – Diffie-Hellman, IPsec – ESP, AH, IKEv1, IKEv2, hashing algorithms MD5 and SHA, and authentication methods
- Describe PKI components and protection methods
- Describe Elliptic Curve Cryptography (ECC)
- Compare and contrast SSL, DTLS, and TLS
Our Process
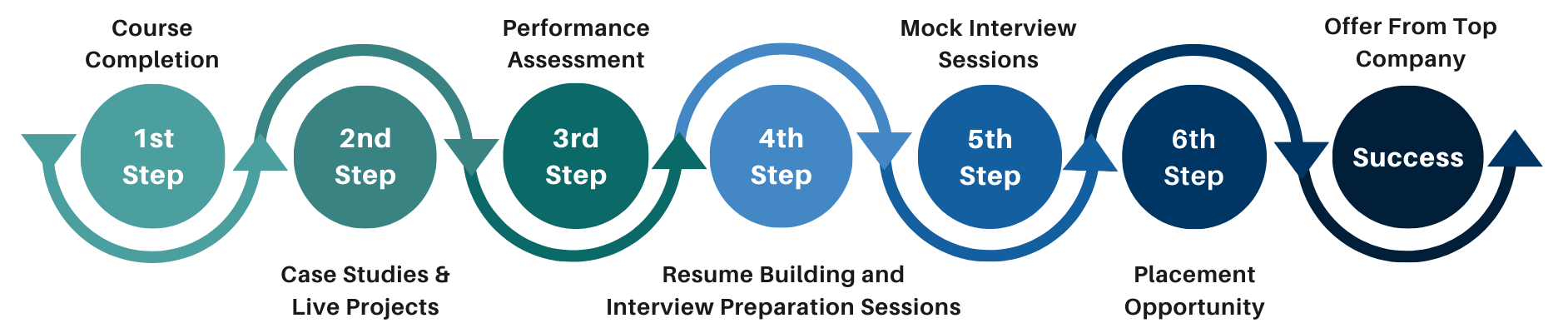
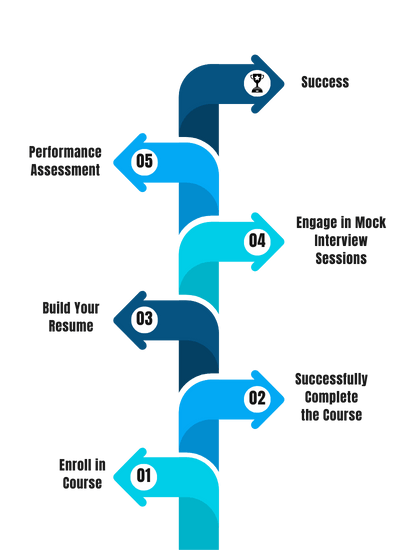
FAQ'S
- Classroom Training
- Online Training
- Corporate Training
- On campus Training
Career Assistance
- Build an Impressive Resume
- Attend Mock-Up Interviews with Experts
- Get Interviews & Get Hired
Training Certification
Earn your certificate
Your certificate and skills are vital to the extent of jump-starting your career and giving you a chance to compete in a global space.
Share your achievement
Talk about it on Linkedin, Twitter, Facebook, boost your resume or frame it- tell your friend and colleagues about it.
Upcoming Batches
What People Say
Our Partners
Need Customized Curriculum? Request Now
Structure your learning and get a certificate to prove it.

Our Clients

Our Placed Students
Related Courses
Review Us
Kanika Gupta
![]() Monday, 01 May 2017
Monday, 01 May 2017
CCNP Security Training In Noida
I have completed my ccnp security training from CETPA . Cetpa is the best institute for all the technologies because it provides the best trainers , live project training, excellent infrastructure and other facilities to their students as well as placement assistance. I am also placed in a very good company because of cetpa so I am really very thankful to all the staff of cetpa.
Course Features
- Lectures 0
- Quizzes 0
- Duration 10 weeks
- Skill level All levels
- Language English
- Students 0
- Assessments Yes